Implementation and operations
Penetration tests
Your challenges
- Have you been, or are you facing cyberattacks?
- Have you performed PenTests in the past, but struggled to communicate the results to your Board/Management Committee?
- Are you willing to assess the effectiveness of your security controls?
- Do you want to make sure your Security Operations Center can react quickly and effectively to cyberattacks?
What does it include
- Attacks from the internal network (malicious employee/ third party, client in a meeting room, etc);
- Attacks from the Internet, targeting exposed infrastructure (public servers, etc.) or employees (phishing, etc.);
- Attacks on mobile devices and mobile applications;
- Any combination of the above, or even specific scenarios tailed to your needs.
Key benefits
- Enhanced confidentiality, integrity and availability of information systems.


Red & Purple team
Your challenges
- Are you willing to test the overall effectiveness of your security infrastructure?
- Have you been, or are you facing sophisticated cyberattacks?
- Are you willing to test your organisation’s ability to respond to advanced attacks through real simulation exercises?
What does it include
- Holistic simulation of advanced attacks on predefined targets;
- (e.g. specific documents or systems) including physical intrusions, social engineering attacks, attacks on Web-exposed systems, etc.;
- Workshops with incident response and monitoring teams to analyse how they detected and reacted at each stage of the attack and identify potential areas for improvement.
Key benefits
- Realistic assessment of your defensive capabilities;
- Demonstrating how a premeditated attack can damage the organisation;
- Identification of critical security flaws in the infrastructure.
Security architecture
Your challenges
- Do you need more assurance about your security technology architecture?
- How do you make sure that your current security capabilities are consistent across the organisation, and aligned with your security strategy?
- How do you best integrate the security tools deployed in your organisation?
- Do you need assistance in developing security architecture artefacts?
What does it include
- Maturity assessment of your IT security architecture against best practices and industry standards (e.g., SWIFT, PSD2);
- Support in the definition of a technical roadmap to achieve a higher level of maturity for specific security capabilities;
- Assistance to security architects in developing security architecture artefacts (e.g., security patterns, principles, security services and solutions inventory, etc.).
Key benefits
- Comprehensive assessment of your security architecture capabilities, based on our framework of best practices and our understanding of your context;
- Better alignment of your security architecture with your security objectives.

Security awareness
Your challenges
- Do you want to raise your staff’s awareness of information security risks?
- Has one of your employees caused a major security breach?
- Are you aware of your internal security processes?
What does it include
- Assessment of your company’s reaction to a fake attack;
- Tailored awareness materials and delivery of the overall awareness program.
Key benefits
- Reduce risk of errors and make all stakeholders aware of what the cybersecurity risks are and how they can be reduced;
- Familiarise people with the appropriate rules and procedures defined by your organisation;
- Thanks to PwC’s Academy (a wholly owned subsidiary of PwC and an approved training organisation), you are entitled to interest subsidies (more information on the INFPC website).

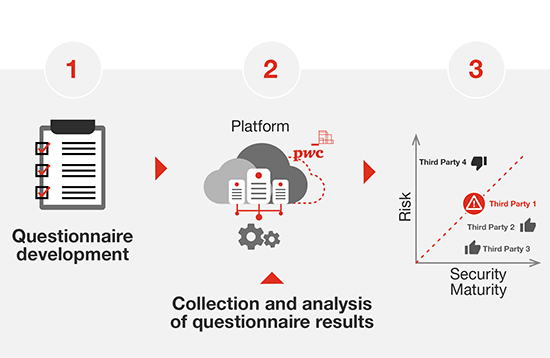
Third party security assessment
Your challenges
- Are you fully aware of your third parties’ security practices, and do you feel comfortable with the level of information security they provide?
- Are you currently in the process of selecting a new service provider and believe that information security criteria should be taken into consideration?
- Are you facing difficulties in assessing the security maturity of your numerous third parties?
- Was a recent security incident imputed to one of your third parties?
What does it include
- A web-platform that will enable you to centrally manage security assessments of your third parties;
- Tailored questionnaires, based on good practices and main international standards to assess your third parties;
- Support in processing questionnaires from third parties to determine their maturity level.
Key benefits
- Accurate, fast and reliable monitoring of third party security.
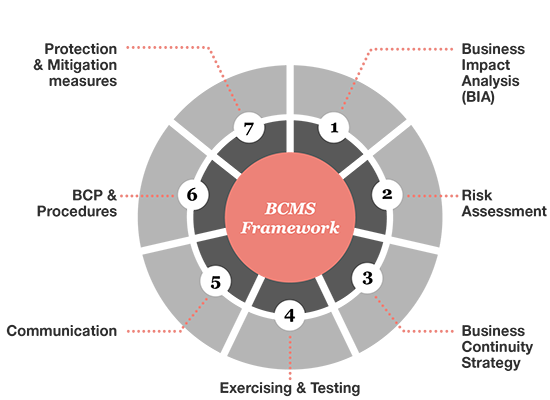
BCMS assessment
Your challenges
- Are you aware of your business continuity risks and their potential impacts?
- Do you know what would be your financial loss in case of business interruption?
- What are the business functions you should recover first?
- Are your key suppliers and service providers viable?
- Does our IT disaster recovery plan support our business recovery requirements?
What does it include
- Implement a business continuity management framework based on ISO22301;
- Execute BIA and risk analysis;
- Develop the business continuity strategies considering the costs and benefits;
- Design BCM policies and procedures;
- Advice in BCM software and service providers selection;
- Support in preparing training, exercise and continuous improvement.
Key benefits
- A team who has 20 years of experience in providing BCM advice;
- The use of our Cyber capacities in your BCMS;
- Be prepared to face the unexpected.